In the previous post, we viewed the results of the assessment with Code Dx. Another tool available in the SWAMP is ThreadFix. Different views of the same data may provide the other perspective needed to better remediate a vulnerability finding.
Let’s get back into the SWAMP!
-
We already have the package ready and assessed, so let’s click on “Results”

Change the viewer from “Code Dx” to “Threadfix”

Scroll down to the package results (in our case OpenSSH 4.3 blog2) and check the far left checkbox. After I did this step, the viewer changed back to “Code Dx”. Make sure your viewer is still set to “Threadfix”.

If you scroll back down, at the time of this writing, only Clang is compatible with Threadfix and the only one that can be checked
Scroll back to the top and click on “View Assessment Results” ensuring that Threadfix is still selected
A new window should open up with a viewer to the results of the scan that’ll use Threadfix
Click on “Latest Analysis Run” for the correct package
After the viewer loads, click on “Scans” at the top
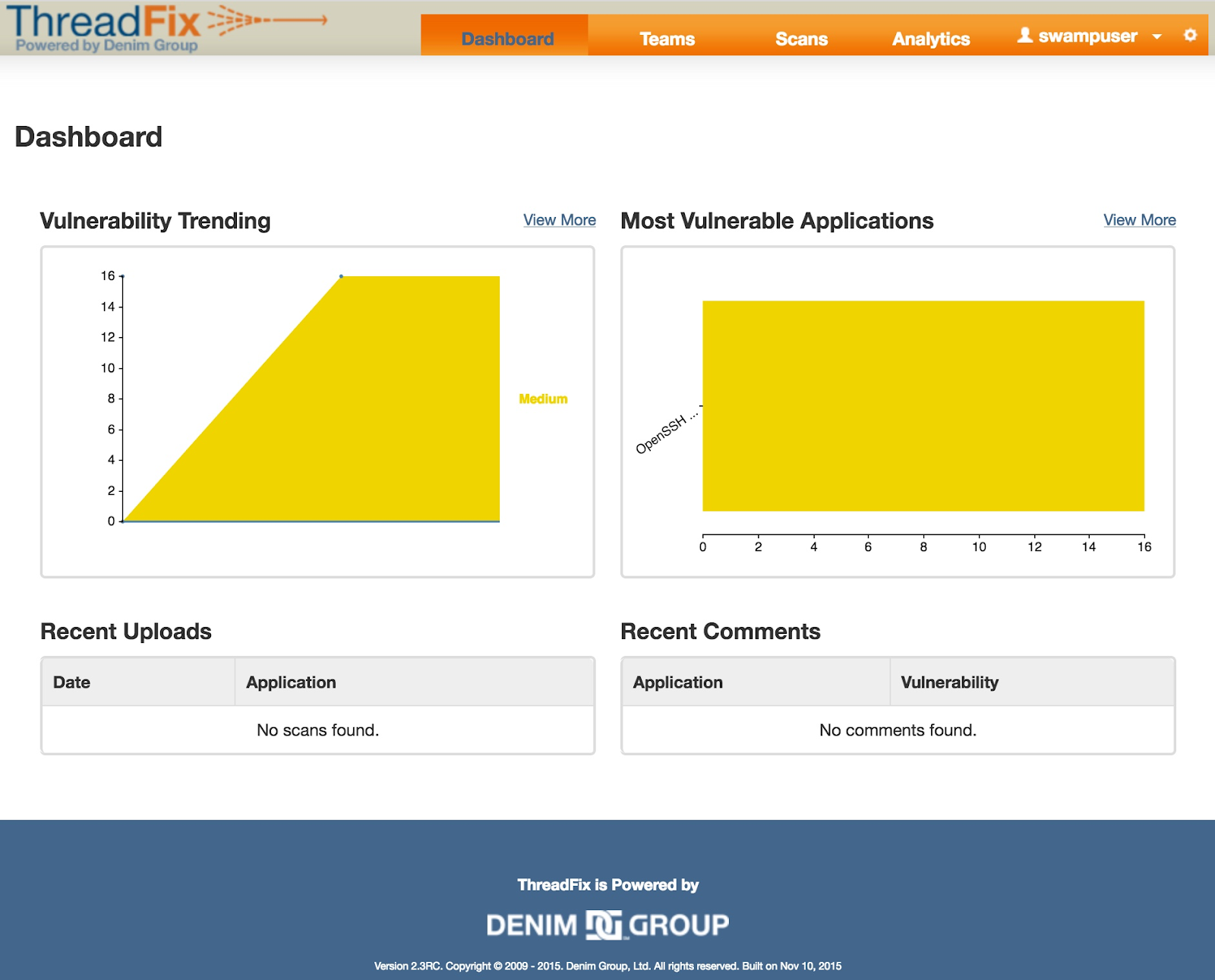
This screen below shows some interesting results. Let’s review the first option with 16 results and click the “View Scan” link.

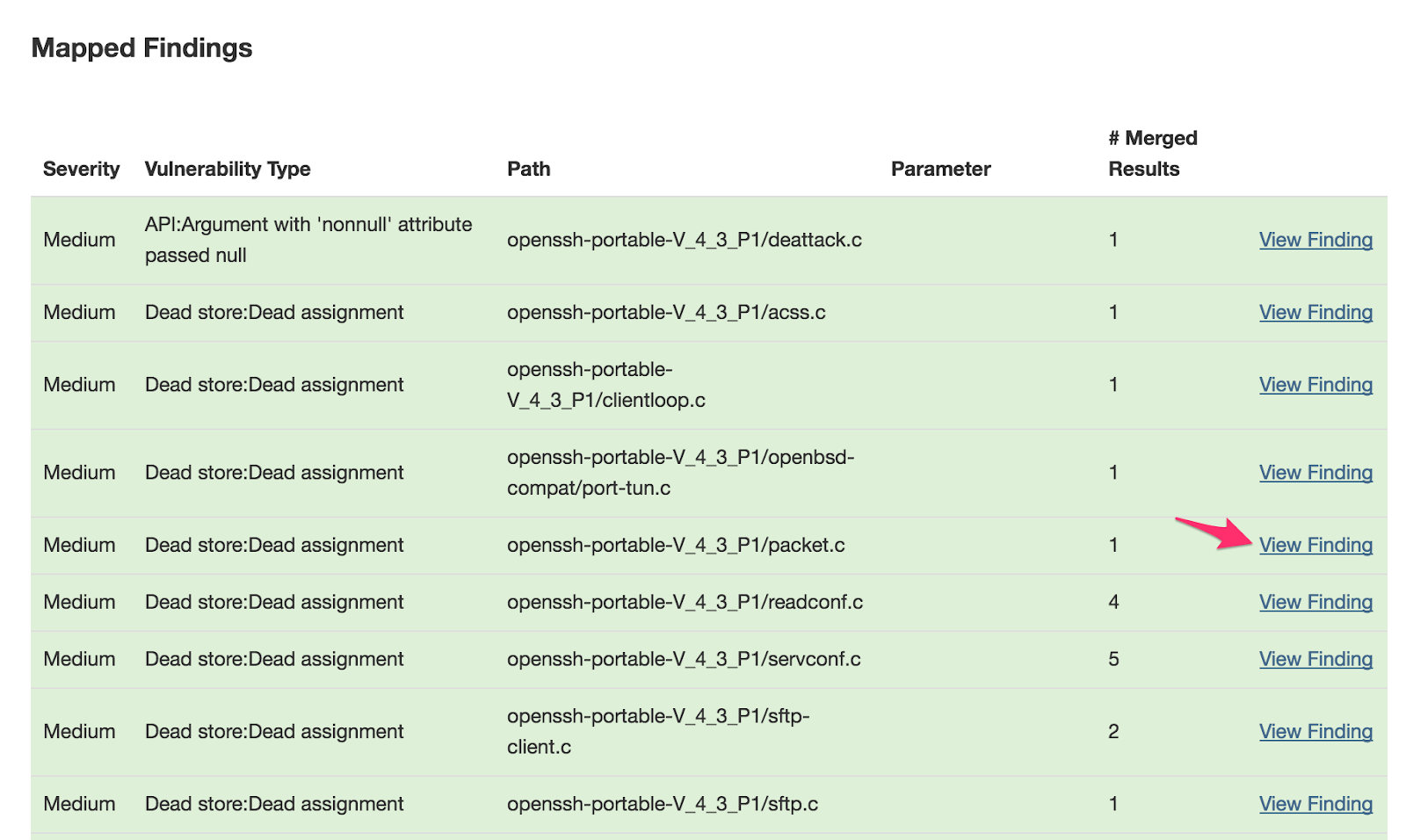
In the “Mapped Findings” screen, we see all of the vulnerabilities from the scan:

Let’s see more detail in the “packet.c” vulnerability finding. Click “View Finding” on this line:
Here we can see additional detail for this finding:

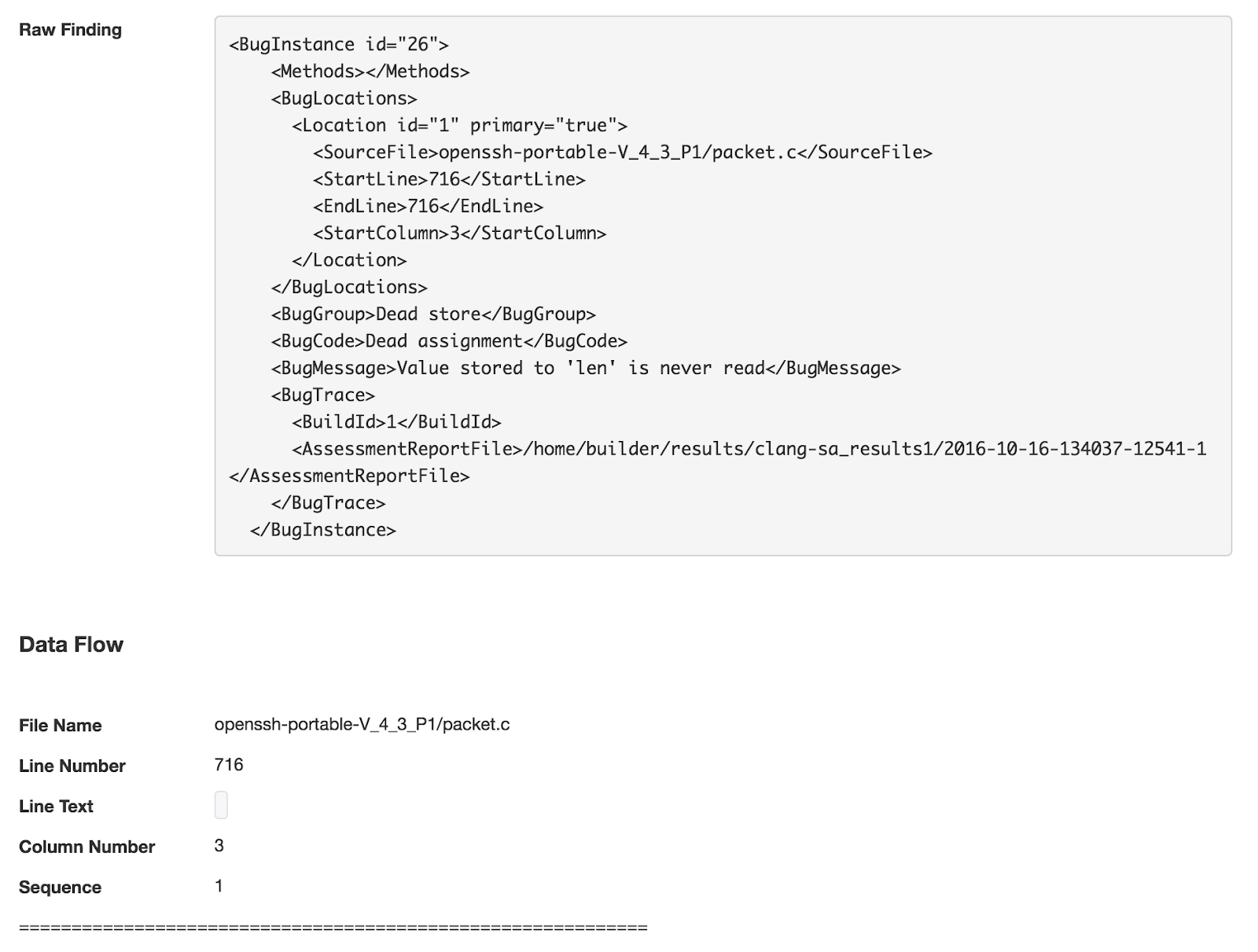
There is not much more to say about this tool and the way we can look at vulnerabilities. Clicking on “Dashboard” at the top will return you to the main Threadfix screen that allows you to drill into vulnerability findings in a variety of ways that can help you track down specific issues.